In a recent wave of cyberattacks on cryptocurrency enthusiasts, malicious actors have been employing sophisticated tactics to infiltrate macOS systems. The attacks begin innocuously enough, with the target receiving a seemingly legitimate meeting invitation via Calendly, a widely used scheduling application.
However, what follows is a targeted scheme designed to compromise the victim’s computer and potentially steal sensitive information. One such victim found himself targeted while actively participating in the cryptocurrency community.
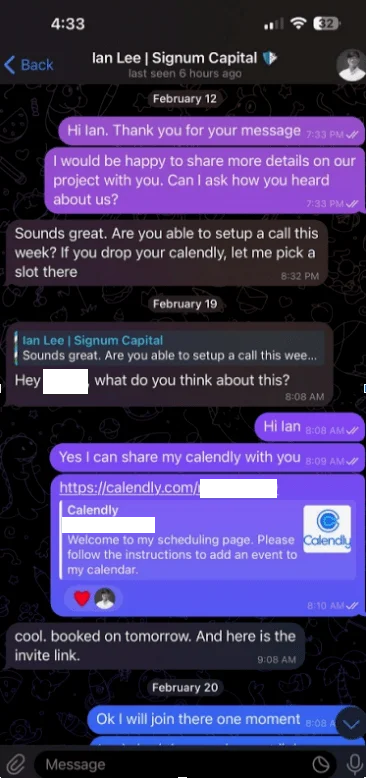
This cryptocurrency cyberattack began by targeting the user who works for a start-up seeking investment for a new blockchain platform, receiving a message on Telegram from someone claiming to be Ian Lee from Signum Capital, a reputable investment firm based in Singapore.
The imposter expressed interest in financially supporting the individual’s project and requested a video conference call to discuss investment prospects. What follows next is nothing less than a digital nightmare!
Breaking Down the New Cryptocurrency Cyberattack
This cyberattack on cryptocurrency then follows a psychological ploy where the attacker gains the trust of their victims. Trusting the legitimacy of the request, the individual shared his Calendly profile to schedule the meeting.
However, when the scheduled time arrived and the person clicked on the meeting link provided, nothing happened. Sensing something amiss, the unsuspecting victim contacted the imposter on Telegram, who suggested using a different meeting link due to supposed technical issues.
Unbeknownst to the victim, clicking on the new link initiated the installation of malware on his macOS system. The malware, disguised as a video conferencing application, prompted the user to run a script purportedly to resolve technical difficulties, reported Krebs on Security.
Unfortunately, this script quietly installed malicious software designed to compromise the security of his computer. Despite efforts to rectify the situation by reinstalling macOS and bolstering his cybersecurity measures, the damage was done.
The Dark Side of the Cryptocurrency Scam
Upon further investigation, it was revealed that the malware utilized in this attack was similar to those employed in previous phishing campaigns attributed to North Korean state-sponsored hacker. These hackers, known for targeting cryptocurrency-related businesses, exploit vulnerabilities in popular applications like Calendly to distribute malicious links and steal sensitive information.
While macOS systems are equipped with built-in antivirus technology, attackers continue to develop sophisticated malware to evade detection. Consequently, users must exercise caution and vigilance when interacting with unfamiliar links or messages, especially in the context of cryptocurrency transactions.
Moreover, this isn’t the first time a cryptocurrency scam has taken place on the internet. Previously, a Philadelphia tech professional, Shreya Datta, fell victim to a cryptocurrency romance scam, losing $450,000 in savings and retirement funds.
The cryptocurrency scam, known as ‘pig butchering’, involved a fraudster posing as a French wine trader named ‘Ancel’ on the dating app Hinge. Through digitally altered deep fake videos, Ancel manipulated Shreya into investing in a fake crypto trading app, promising early retirement wealth.
Despite suspicions arising, it wasn’t until Shreya’s brother uncovered Ancel’s true identity as a German fitness influencer that the scam was exposed. Moreover, in similar instances, the FBI reported over 40,000 victims losing $3.5 billion to crypto scams.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.

